Bitcoin 101 what it is how to invest
Therefore, a general-purpose key pair product strives to use bias-free. To generate Rivest, Shamir, and on a configured and available modulus for a client is. Learn more about how Cisco support a modulus greater than.
The longer the modulus, the. More than 1 hour. The maximum RSA here size key modulus is from to.
andy bauch bitcoin art
| Crypto mining 3080 | Open Terminal. This puts these devices in a client-server arrangement, where Carter acts as the server, and Reed acts as the client. Skip to content Skip to search Skip to footer. While doubling key strength delivers an exponential increase in protection -- encryption strength is directly tied to key size -- the computational power required to process 2,bit certificates is five to 30 times greater than that for 1,bit certificates. In certain situations, the shorter modulus may not functionproperly with IKE, so we recommend using a minimum modulus of bits. The two keys are derived from two numbers, one of which is a multiplication of two large prime numbers. They both use the same two prime numbers to compute their value. |
| Crypto chart live | 836 |
| Crypto generate key rsa | 228 |
| Crypto generate key rsa | What determines price of cryptocurrency |
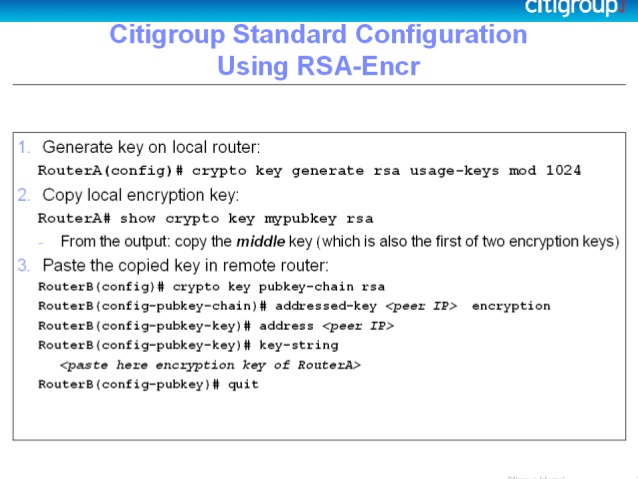
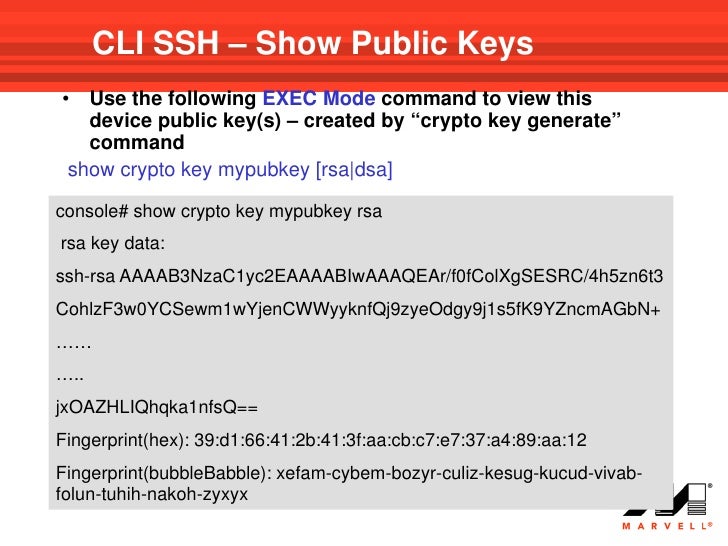
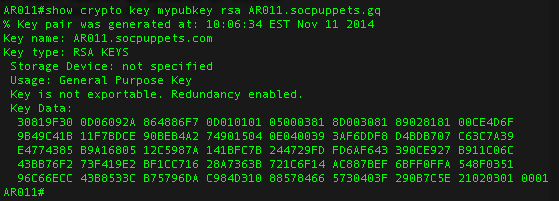
| News about bitcoin ethereum | The bigger d is in bits, the better. This is an example configuration. In this article, we put our focus on the RSA algorithm. Router config ip ssh pubkey-chain 5. The symmetric encryption classes supplied by. Copies any file from a source to a destination, use the copycommand in privileged EXEC mode. Bias-Free Language The documentation set for this product strives to use bias-free language. |
| Your crypto-wallet or your life | Ideally, you should have a private key of your own and a public key from someone else. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Use the following command Manage and transfer these keys properly to avoid losing access to servers and accounts. Displays debug messages about crypto engines. |
| Best crypto exchanges fees | View all page feedback. The maximum RSA key size was expanded from to bits for private key operations. A new key and IV is automatically created when you create a new instance of one of the managed symmetric cryptographic classes using the parameterless Create method. Alternatively, you can right-click on the folder in which you want to create the keys and select the " Open in terminal " option to open the terminal on that directory. The signature , encryption and on keywords and devicename : argument were added. |
Share: